
20 December 2000. Thanks to Anonymous.
Date: Tue, 19 Dec 2000 20:34:34 +0000
To: jy@jya.com
Subject: CWAN, JWID, TEMPEST, Crowley
Dear Sir
I have recently discovered Cryptome, and have found it an excellent resource since I have a keen interest in matters of intelligence. I am particularly interested the ECHELON system and its implications, as described in the STOA report.
I have work experience at DERA PDW CDA(S/A) AWW. This long and rather confusing acronym stands for the Defence Evaluation Research Agency, Portsdown-West, Centre for Defence Analysis (Sea/Air), Above Water Warfare. I would rather not go into the details of my work experience, just in case I breach any agreements I had. However, I made some interesting discoveries prior to my work experience when I did some research on the internet.
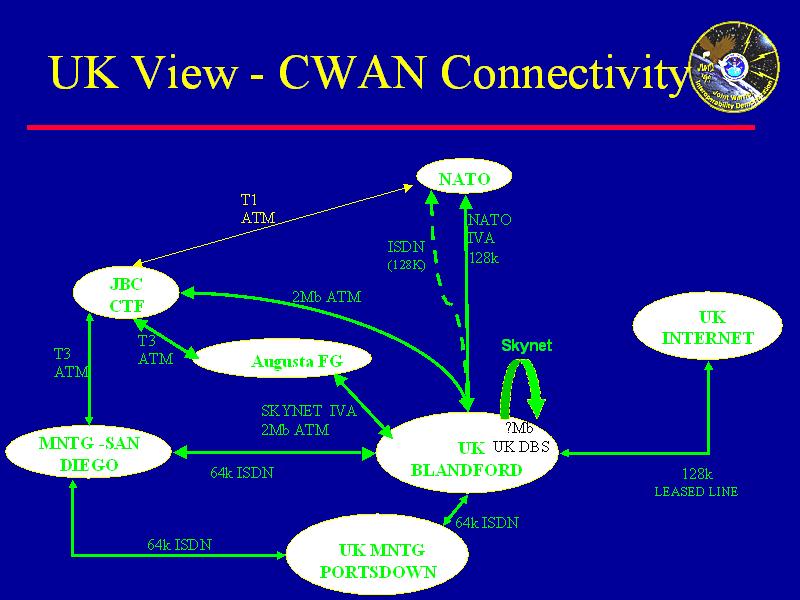
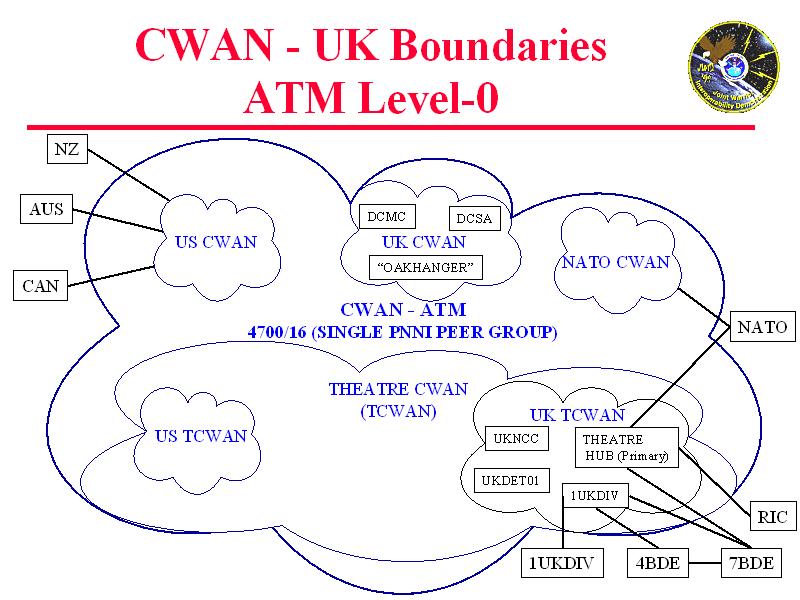
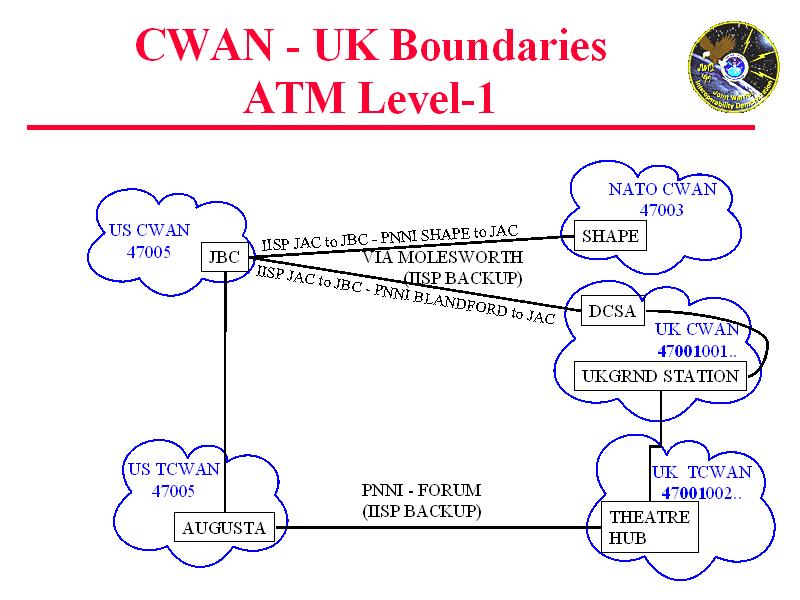
After searching for DERA Portsdown-West, I found some information on the JWID '99 exercises. JWID stands for Joint Warrior Interoperability Demonstration, and the exercise involves a theoretical look at defence ideas. All the 'COALITION' countries (i.e. the countries from the UKUSA agreement) are involved. Incidentlally, I was involved in some data entry for the JWID 2000 exercise during my work experience. The interesting thing I discovered was something on the CWAN - Coalition Wide Area Network.
I've attached some diagrams from a presentation I found on the Net, showing the connectivity. Is this somehow to do with the distribution part of the intelligence cycle? Is it part of the Echelon system? Any ideas?
At DERA Portsdown-West, there were a series of large antenna. During my health and safety briefing, I was told that they weren't dangerous as long as I did not go too close to them, because when they are 'transmitting' they give off a lot of radiation. There were about three or four of them, each consisting of a central mast with a number of wires coming off of them.
Also during my research, I found some information on the UK Security Policy for the JWID exercise. I have also attached this, since it contains references to TEMPEST countermeasures, radiation security, and other intersitng electronic systems. It also says of DERA PDW;
"DERA Portsdown West, Hampshire. Portsdown West provides communications connectivity for the UK portion of the MNTG at Blandford to the rest of the MNTG demonstration. This is primarily achieved through a link to San Diego."
Anyway, I hope this is of some interest. Another point about your site, in particular The Crowley Files. One of the people in the Crowley Files, is;
"Kobernicki, Lesek59 Elmleigh Rd., Hampshire, PO 0 2AB, England" [See message below from alleged "Kobernicki."]
This name is not on NameBase, and they live fairly close to me. Any idea of their role as a source for the CIA?
If any of the information is of interest, you can publish them, but please leave my email address and name anonyous.
--------------------------------------------------------------------------------
REFERENCES
JSP 440 Vol. III, IT Security.
CESG Electronic Information Systems Security Memorandum, Number 5: System Security Policies, Issue 3.0, July 1994.
HMG Information Security Standard, Assurance Requirements for IT Systems, April 1998.
BTR/01/3(91) - Minimum Standards for TEMPEST Countermeasures, Issue 2.0, June 1992.
BTR/01/200(3) - Radiation Security of Communications and Data Processing Installations, Issue 3.0, Amendment No.7, November 1994.
CESG INFOSEC Memorandum No. 7: Re-Use or Disposal of Computer Memory and Magnetic Store, Issue 2.0, August 1995.
CESG COMPUSEC Manual N - Vulnerabilities of the TCP/IP Protocol Suite, Issue 2.0, January 1999.
CESG INFOSEC Memorandum 13: Protecting Government Connections to the Internet, Issue 4.0, November 1997.
JWID99 Coalition Security Requirements Statement.
Annex L to JWID 99 Operation Plan - Security
PURPOSE OF THIS DOCUMENT
This Appendix expands upon and supplements the general statement of security requirements in the Coalition Security Requirements Statement (Reference I) and the security enforcing mechanisms described in Annex L of the JWID99 Operations Plan (Reference J).
SCOPE OF THIS DOCUMENT
This Appendix describes the security policies and procedures, which will apply to all aspects of UK JWID99 operations in order to meet the security requirements of the UK Ministry of Defence (MOD).
Reference A is the primary document which provides guidance for operations under JWID99, for all aspects of physical, procedural, personnel and document security. Technical COMPUSEC and COMSEC guidance in Reference A must also be adhered to, subject to the statements in this document concerning the applicability of related CESG documentation (see below).
The guidance contained in Reference B concerning the format and content of security documentation applies to relevant documents produced for JWID99.
Reference C does not apply in the general case for systems connected for the purposes of JWID99. The Joint Warrior Interoperability Demonstration is an exercise designed to develop and promote emerging technologies. Taking into account the nature of the environment, the UK Accreditor has agreed that there is no formal requirement for assurance in any of the IT components.
References D and E apply to all equipment processing protectively marked information released to participants located at UK Government sites.
Reference F contains specific information related to the issue of purging equipment post-JWID.
References G and H should be taken as supporting information.
References I and J provide the basis for the UK interpretation of the JWID security policies. Where Annex L of the JWID 99 Operation Plan is in conflict with UK policy on information security, the UK rules are to take precedence.
RESPONSIBILITIES FOR SECURITY
The UK component of JWID99 will be managed by a Steering Group chaired by AD JBD, Col Philip Pratley.
Overall responsibility for security in the UK component of JWID99 has been delegated from the Steering Committee to the Project Manager, Wg Cdr David Ward.
Below the Project Manager, a number of Working Groups manage specific aspects of JWID99 on behalf of the Project Manager and provide specialist advice. In particular, the UK Accreditation Authority chairs the UK Security Working Group.
The Accreditation Authority for equipment based on UK Government sites is Mr Ian Bryant, DSy(Pol), who can be reached on (0)171 218 4505. The responsibilities of an Accreditation Authority are formally defined in JSP440.
The UK Security Assurance Co-ordinator (SAC) for JWID99 is Mr David Freeman, who can be reached on (0)1252 723672. The responsibilities of the SAC are:
To develop and agree with the UK Accreditor, the UK contribution on security to the JWID99 Operational Plan (OPLAN). To develop and agree with the UK Accreditor, site-specific security requirements for UK Government sites hosting equipment participating in JWID99. To develop and agree with the UK Accreditor, Security Operating Procedures (SyOPs) for the UK demonstrations being undertaken for JWID99. To carry out such other security related tasks as may be assigned by the Accreditor and by the UK JWID99 management. In addition, a UK JWID Sites Security Manager (SSM), Mr David Freeman, will be appointed prior to the start of JWID99. The responsibilities of the SSM are:To ensure that the UK National security policy for JWID99 is upheld, by monitoring and reporting upon compliance with this policy and with demonstration SyOPs at all UK JWID99 sites. To liase with the UK Accreditor on matters of security during JWID99 execution. To liase with local site security officers on issues of personnel clearances and physical security. To act as a first point of contact for users of the UK component of JWID99 on matters of security. To maintain a register of reported security related events affecting the UK component of JWID99, and to bring the contents of the register to the attention of the Accreditation Authority at an appropriate time depending on the nature of any one or any combination of events.
LOCATION OF UK JWID99 EQUIPMENT
The UK sites, and those of the other participating JWID99 partners (Australia, Canada, NATO, New Zealand, and the United States) will be linked by a Coalition Wide Area Network (CWAN).
Equipment for JWID99 will be located at the following sites in the UK:
Army CIS Services Group, Blandford Camp, Dorset. Blandford is the designated primary site for UK participation in JWID99, and will host demonstrations of, GP3, CHOTS and other systems and in particular the UK portion of the Multi-national Task Group (MNTG) demonstration. The main link from the UK to the Coalition Wide Area Network (CWAN) will reside at Blandford. DERA Portsdown West, Hampshire. Portsdown West provides communications connectivity for the UK portion of the MNTG at Blandford to the rest of the MNTG demonstration. This is primarily achieved through a link to San Diego.
SYSTEM CONFIGURATION
The configuration of the UK component of JWID99 is liable to changes arising from the need to gain maximum benefit from this annual opportunity to learn and improve. The overall system configuration at any time can be obtained from the Chair of the Technical Working Group, Mr Ian Cassell, who can be reached on (0)1684 894587.
MODE OF OPERATION
Coalition Wide Area Network
The JWID99 Coalition Wide Area Network (CWAN) security mode of operation is Dedicated Secret.
There are no facilities for segmentation of JWID data released onto the network: all information released onto the CWAN is considered to be releasable to all participating nations.
UK Component
That segment of the UK component of JWID99 which is connected to the CWAN will operate in a security mode of Dedicated Secret.
Within an individual system or demonstration there may be a requirement to enforce a need to know. This could be for reasons of maintaining commercial confidentiality, for the purposes of the demonstration itself, and/or to maintain integrity of demonstration software and/or data. Implementation and operation of these business level controls fall to the demonstration operator, and are considered to be outside the scope of this security policy.
Within an individual system or demonstration there may also be a requirement to enforce access control over information which is not releasable to the CWAN. In these cases, providing that suitable functionality is available on the demonstration platform, the equipment may be connected to the CWAN (subject to Accreditor approval) and an appropriate release mechanism defined. Where such functionality cannot be provided, or where information marked above SECRET or which carries with it a strong need to know is being held, then standalone operation or the use of a Virtual Private Network based on encryption, may be mandated by the Accreditation Authority.
There are no non-UK (such as NATO-only) demonstrations envisaged for the UK component of JWID99: all demonstrations will be accessible to UK nationals subject to the appropriate clearance.
PROTECTIVE MARKINGS
The CWAN has been accredited by the JWID99 Coalition Approval Board to operate at SECRET JWIDCO, where JWIDCO has been defined (Reference I) as JWID COALITION. However the UK Accreditation Authority has decreed that no UK data or applications attracting a protective marking above RESTRICTED will reside on any systems directly or indirectly connected electronically to the CWAN.
All UK participants are reminded that there is no functionality on the CWAN that will enforce separation on the basis of information labels. Where a system connected to the CWAN has a requirement to process information which cannot be released onto the CWAN itself, appropriate security functionality must be provided in the end system, together with supporting procedural measures.
Demonstration data released onto the CWAN must carry information labels advising recipients of release conditions. Information labels must consist of:
Originator. For all information originated in the UK this will be "UK", unless it has been released from a NATO source operating from a UK site, when it will be "NATO". Classification. The CWAN will process information with protective markings up to and including SECRET. It is important to note that systems connected to the CWAN will process information which relates to the scenario in play, and which therefore may be considered to be only notionally classified, and also "real world" classified information. There is no means by which these two types of information can be distinguished, and therefore all information processed on machines making up the UK component of JWID99 must be assumed by default to be classified SECRET. The marking "JWIDCO", which indicates that the information is releasable to all members of the JWID99 Coalition. Release. In addition, as advisory markers, the label may carry text such as "UK/US Eyes Only". At the termination of JWID99, all information held on systems making up the UK component of JWID99, and marked "JWIDCO" will be considered to be classified at the level indicated by the label less the JWIDCO marker, or UK SECRET by default.
INTERCONNECTIONS
Demonstration UK70 will have a connection to the Internet. Approved security devices that only permit the importing of information to the CWAN will protect this connection. No information will be exported through this interconnection. In addition only certain types (protocols) of information will be imported and these will be subject to content checking and anti-virus scanning.
30 Demonstration UK31 consists of a secure paging system. However, the cryptographic device associated with this system is only approved for passing information up to and including Restricted. Consequently a security device will be placed between the CWAN and UK31 that permits small text-only information to be exported from the CWAN. The content of these messages will be verified to ensure that they do not contain any information greater than Restricted.
Although no other interconnections are planned to the UK component of JWID99, the configuration of the network at any time can be obtained as part of the overall system configuration description.
SECURITY ENVIRONMENT
By its very nature, the JWID exercise will inevitably highlight weaknesses and constraints applying to the operational resources of the United Kingdom and her allies. This information could be of interest to a number of agencies including journalists who wish to access information other than their open source briefings, information brokers, and to a degree, other interested agencies such as techno-anarchists.
The threat of deliberate attack by Hostile Intelligence Services in order to gain intelligence and/or disrupt the demonstration is considered to be low.
The risk of terrorist action is considered also to be low: disruption of JWID99 is not likely to lead to the achievement of any specific political goal in respect of UK mainland sites.
Nor is JWID considered to be a fruitful target for organised crime.
Disgruntled or malicious operators are not considered to be a threat in this case, since some operators will be acting on behalf of equipment providers (their employers) and others will be Service and other Government personnel acting in full view of their peers in the CIS community. However, the cultural environment for JWID is likely to prompt individuals to attempt to exceed their normal authorisations. Although malice is unlikely to be a factor, inquisitiveness and the desire to learn as much as possible almost certainly will be.
Although it is not one of the stated objectives for JWID, the exercise acts to some extent as a showcase for Industry capability. There is a corresponding risk that participants may be tempted to gather industrial intelligence through illicit means and/or breach copyright. We consider this risk to be low, on the grounds that most suppliers will have or will be seeking to establish a long term relationship with the UK MOD and would not wish to compromise that objective by embarrassing their hosts.
Accidents and unforeseen circumstances leading to denial of service are considered to be likely threats within the environment for JWID99. Although it is unlikely that UK National interests would be damaged by such an event, it could nonetheless reduce the level of benefit gained from conducting the exercise.
Given that media and data exchanges will form a large part of the day to day operations of JWID, the risk of infection from malicious software is considered to be high.
OVERVIEW OF SECURITY REQUIREMENT
Given that all information carried on the CWAN is considered accessible to all participating nations, and taking into account both the stated objectives for JWID99 and the preceding discussion on threats to UK based assets, the primary objectives of the security measures applying to the UK component are stated as:
To ensure that all protectively marked material processed on the UK component is handled in accordance with its marking both during and after the demonstration. To provide an appropriate level of security which is visible to Coalition partners, so that all participants may exchange information with confidence. To assist with the achievement of a successful demonstration, by providing a level of security which contributes to the smooth execution of JWID99.
SECURITY MEASURES
Overview
The nature of the environment for JWID precludes any significant degree of reliance on purely technical measures. Protection of the UK component will therefore rely primarily upon physical security, user awareness and procedural controls:
For each site hosting UK based assets for JWID99, an individual will be nominated to act as JWID Site Director. It is the responsibility of the UK JWID Project Manager to assign individuals to these posts. The measures described in this document under the heading of ‘Global Security Environment’ relate to sites hosting UK based assets for JWID99. It is the responsibility of each JWID Site Director to obtain formal agreement from the local site security manager that the requirements can be met in full for the site in question. Where there is doubt or shortcomings then these are to be raised with the JWID SAC who will if necessary liase with the Accreditor. The measures described in this document under the heading of ‘Local Security Environment’ relate to the operation of the room or building housing UK JWID99 equipment. It is the direct responsibility of the local JWID Site Director to see that these measures are enforced. The results of previous exercises, surveys and studies show that a major weakness in security arises from inadequate system management. Attempting to enforce strict configuration control is unlikely to be a successful strategy for JWID: however, all UK JWID99 demonstration operators (encompassing commercial equipment suppliers, service providers, users and those responsible for conducting demonstrations on previously installed equipment) are required to operate within the constraints of Security Operating Procedures. The framework for these SyOPs is provided in this document under the heading ‘Demonstration SyOPs’.
Global Security Environment
The instructions in this section relate to the physical and procedural measures applied to the site hosting UK components of JWID99. As such they constitute the basis of an agreement between the JWID Site Director and the local site security staff.
All UK sites hosting components of JWID99 will provide as a minimum, the level of physical protection defined in JSP 440 for sites processing SECRET information.
Procedures at the entry to the site will ensure that only individuals with a clearance of Security Check (SC) or above are granted unescorted access to the site. All other visitors will be met by their sponsor and escorted by a representative of their sponsor, whilst on site.
A record will be maintained of all visitors attending the site.
All visitors attending the site will be required to wear badges indicating their status, whilst on the site.
Spot checks will be carried out on the exit points from each site, to detect deter and prevent the unauthorised removal of equipment.
Local Security Environment
The instructions in this section relate to the responsibilities of the JWID Site Director, and constitute a set of Terms of Reference (TORs) for the security aspects of the role.
The JWID Site Director will gain the agreement of the local site security manager that the minimum site requirements for JWID can be met, and will document the agreement, and copy it to the Accreditation Authority.
All terminals, servers and communications equipment for UK components will be secured in rooms with controlled access (the JWID Area). The JWID Site Director or an individual acting on their behalf is responsible for administering access to the JWID Area.
Only individuals with a security clearance of SC or higher will be granted unescorted access to the JWID Area. It is the responsibility of the JWID Site Director, with the support of the SSM, to ensure that clearances are confirmed as adequate before granting unescorted access.
Where personnel are to be granted free access to the JWID Area for the duration of the demonstration, the JWID Site Director is responsible, with the support of the SSM, for confirming clearances and issuing JWID passes.
The JWID Site Director or an individual acting on their behalf, is responsible for maintaining a record of visitors (individuals without JWID passes) to the JWID Area. This record will include date, times, name, organisation and purpose of visit.
When visitors who are not cleared to SECRET are allowed escorted access to the JWID Area, the JWID Site Director (or an individual acting on their behalf) is responsible for alerting JWID operators to this fact.
All equipment which has been used to store or process data marked CONFIDENTIAL or higher is to be stored in appropriate security furniture when the JWID Area is unmanned. Keys and combinations are to be held under the control of the JWID Site Director or a responsible individual acting on their behalf.
In view of the nature of the JWID environment, there is no requirement for classified document registration, providing that the document remains within the JWID Area and is securely disposed of. If material is to be removed from the JWID area which is at the level of CONFIDENTIAL or above it must be registered in a Classified Document Registry (MOD Form 102) and a receipt issued if appropriate. Maintenance of the classified document registry is the responsibility of the JWID Site Director or an individual acting on their behalf.
The JWID Site Director is responsible, with the support of the SSM, for ensuring that appropriate document destruction facilities are provided within the JWID Area for the duration of the demonstration.
All communications lines connected to UK components of JWID99 will be protected with an appropriate level of encryption before leaving the JWID Area. Management and handling of encryption devices and associated cryptovariables will be in accordance with MOD regulations as defined in JSP 440, and prevailing CESG advice. It is the responsibility of each JWID Site Director to ensure that an appropriately trained Crypto Custodian is appointed for the site.
The JWID Site Director is responsible for the management of the Local Area Network (LAN) used at each UK JWID99 site:
Spare LAN ports are to be disabled, in order to increase the effectiveness of the procedural controls relating to local configuration management. For similar reasons, where practicable and particularly during the operational phase of JWID99, LAN patch panels, concentrators and switches are to be housed in lockable cabinets, the keys to which will be held under the control of the JWID Site Director. Changes to the LAN configuration must be approved in advance by the JWID Site Director or responsible individual acting on their behalf. No equipment will be connected to the local network, disconnected from the local network, nor removed from the JWID Area without the prior permission of the JWID Site Director. Figure 1 shows the responsibilities of the JWID Site Director in respect of equipment authorisation.
In the event of an emergency evacuation, the JWID Site Director will make a judgement as to whether or not power isolating switches should be thrown. The JWID Site Director must ensure that all personnel are clear of the room before, if appropriate, switching off the power. When all personnel are clear of the area, the door is to be closed and locked.
Demonstration SyOPs
The following section provides guidance to operators of the UK component of JWID99. This guidance applies to commercial equipment suppliers, service providers, system users and those conducting demonstrations on equipment previously installed. The instructions given here, taken together with the demonstration-specific SyOPs issued by the SAC, constitute the security rules governing the conduct of all UK JWID99 demonstrations.
All operators must note that although demonstrations may be operated and configured by or on behalf of Defence organisations or commercial companies, the security of the UK component is the responsibility of the UK Project Manager, delegated in part to the JWID Site Directors. Adherence to the standard and specific SyOPs is therefore mandatory.
Operators must be aware that the process shown in Figure 1 must be followed for all equipment used on UK components of JWID99 prior to operation:
The SAC will issue a Form 1 to each demonstrator operator. When completed the Form 1 will contain equipment details allowing the JWID Site Director to ensure that the demonstration is managed in a secure manner. The operator completes the form and returns it to the SAC who registers the demonstration and assesses the security requirements. Where standard equipment such as NT servers and workstations, UNIX servers, communications switches, portable computers, Web servers and Windows PCs are used, a standard set of SyOPs will be issued to cover the operation of the equipment. Where specific instructions are required (a decision based on the SAC’s assessment of the completed Form 1), these will be drawn up in consultation with the Accreditation Authority, and issued to the operator. Once the necessary SyOPs have been received and acknowledged by the demonstration operator and their local security controller, live operation may proceed. Approval to remove the demonstration from the JWID Area at the end of the demonstration period follows a reverse sequence. The SSM and JWID Site Director confirm that the SyOPs criteria for a secure conclusion have been met, and formally sign off the demonstration. The equipment may then be removed from the JWID Area and from the site.
Operators are reminded that no equipment may be connected to the local network, disconnected from the local network, nor removed from the JWID Area without the prior permission of the JWID Site Director.
All classified material including disks, documents and archives relating to the UK component of JWID99 must be stored and handled within the JWID Area in accordance with the protective marking applied to them.
All items of magnetic media used on servers and workstations must be clearly labelled with the protective marking applying to the data held. The default protective marking is SECRET JWIDCO.
All items of magnetic media loaded whilst write-enabled must be handled according to the highest protective marking of data held on the processor, namely SECRET JWIDCO. In general this will preclude its removal from the premises, unless the JWID Site Director or an individual acting on his behalf can be sure that either: no data has been transferred onto the disk; or that the data can be removed in a way which accords with MOD guidelines; or that the item will be appropriately handled and disposed of.
Where diagnostic software is loaded from an item of magnetic media, that item should be write-protected during the period for which it is mounted. If this is not possible then the item must be considered to hold SECRET JWIDCO data when removed from the machine, and must be handled appropriately.
When no longer required, items of magnetic media and documents must be destroyed in accordance with the protective marking of the data they contain.
Operators should note that equipment connected to the CWAN is assumed to have held data at SECRET JWIDCO by default. Unless an approved method of downgrading the storage on the machine can be provided, the equipment must be returned post-JWID to an environment that will provide an adequate level of security.
Operators are reminded that the maximum level of classification of data to be transferred using the JWID CWAN is SECRET, and that all information to be transferred is considered releasable to all participating nations. Equipment which has been used to process material which is not releasable, or which has been used to process material above the level of SECRET, must be notified to the JWID Site Director well in advance of any intention to connect.
In view of the nature of the JWID environment, there is no requirement for classified document registration, providing that the document remains within the JWID Area and is securely disposed of.
All regular occupants of the JWID Area must have an appropriate level of security clearance, together with a bona fide reason to access the area. The JWID Site Director will check clearances for individuals nominated by the operators; however, operators should be aware that the checking of clearances could take some time.
When visitors without the necessary clearance to access material marked SECRET are granted access to the JWID Area, all operators will be informed of this fact. It is the responsibility of each operator to ensure that safeguards are implemented which prevent protectively marked material from being accessed by those who do not have either the necessary clearance or a need to know.
Operators wishing to bring material classified at CONFIDENTIAL or higher into the JWID Area, and remove it afterwards, must ensure that they have documentation, which proves that the material did not originate from with the JWID Area. If such documentation cannot be provided then the material may in some circumstances be removed and destroyed under the supervision of the JWID Site Director.
Wherever the operator can amend the software configuration of a machine, the operator will provide either a quarantine machine to virus check all disks used on the JWID machine, or will ensure that the JWID machine has virus checking software installed. If it becomes apparent that any machine used for a UK based JWID99 demonstration has been affected by a virus, or any other form of malicious software, or anti-virus checks expose the presence of a virus, the following action is to be taken:
a. immediately inform the SSM, who will inform the JWID Site Director;b. isolate the infected disk by sealing it in an envelope and mark the outside as follows: "Contains virus-infected disk"
c. where the disk is one of a batch from the same source, the entire batch must be isolated;
d. the source of the disk should be identified if possible;
e. do not switch off the machine until directed to do so. Prevent further use of the machine by others;
f. the affected machine must not be used again until a competent person can confirm that it is free of any virus.
Operators must not bring portable telephones, laptop computers that are not related to the demonstration, cameras or recording equipment into the JWID Area. Receive-only pagers however will be permitted. Portable telephones are permitted during the set-up phase prior to the CWAN being declared live on the 12th July 1999.
Operators should familiarise themselves with the names and contact numbers for the SSM, and the JWID Site Director and deputies. All suspected or actual breaches of these instructions and/or specific SyOPs must be reported without delay to the JWID Site Director, or in their absence to the SSM.
In the event of a general failure of the mains power supply, there will be a number of actions that should be taken by the individuals present, in order to ensure that security of the system is not put at risk. These instructions relate only to the security of the system, and are in addition to any general operating procedures to be adopted in the event of power failure:
shut down equipment in a secure and orderly manner;if it has not been possible to conduct an orderly shut-down of all devices, then all devices should be physically switched off so that they are in a known state when power is eventually restored;
In the event of an emergency, the safety of staff should take priority at all times. Individuals should not take any action that would prejudice their personal safety. Where possible, users should switch off terminals and printers, remove removable media, and remove hard-copies from the printer. These should then be locked in the approved security furniture. The System Administrator should attempt to shut down the system in an orderly manner. This procedure should only be attempted where time permits and there is no danger to health and safety.
(Advisory) The operator is responsible for ensuring that users are made aware of their responsibilities in the event of a hardware or software failure.
(Advisory) Backup schedules should be implemented with the aim of losing no more than one day’s work in the event of a compete loss of online data. Preferably this should consist of incremental daily backups, with full weekly backups carried out to a fresh set of tapes for each week of the demonstration period. Backups must be stored securely in the JWID Area. The risk of a complete loss in the event of a fire in the JWID Area is considered to be outweighed by the need for rapid access in the event of a local system failure.
(Advisory) The operator should maintain a supporting backup log. This log records the instigation of a backup, changes to the backup schedule, and the loading/unloading of backup tapes. Each entry identifies as a minimum:
a. the date and time;b. the operator performing the action;
c. details of the action.
Backups may be carried out overnight, providing that the JWID Area is secured. The operator is responsible for ensuring that the backup was successful, and for monitoring for signs of interference or tampering.
Only individuals nominated by the operator should have the privilege to recover user or system data from the backup tapes. All requests for recovery should be directed to an individual nominated by the operator. Following recovery from a system problem the operator is responsible for ensuring that the access controls on recovered files are set appropriately.

From: "Leszek Kobiernicki" <leszek@kobiernicki.freeserve.co.uk> To: <jya@pipeline.com> Subject: " Gregory Douglas " Date: Wed, 20 Dec 2000 06:45:54 -0000 Organization: Educational Consultants ( Oxford ) MI6 here identified my Stahl ( AKA GD ) as a faker extraordinaire. Somehow he seems to have set America by the ears. Why so ? Does no-one hear us any more ? Regards, Friends.